Defensive Research, Weaponized: The 2025 State of Pipeline Security
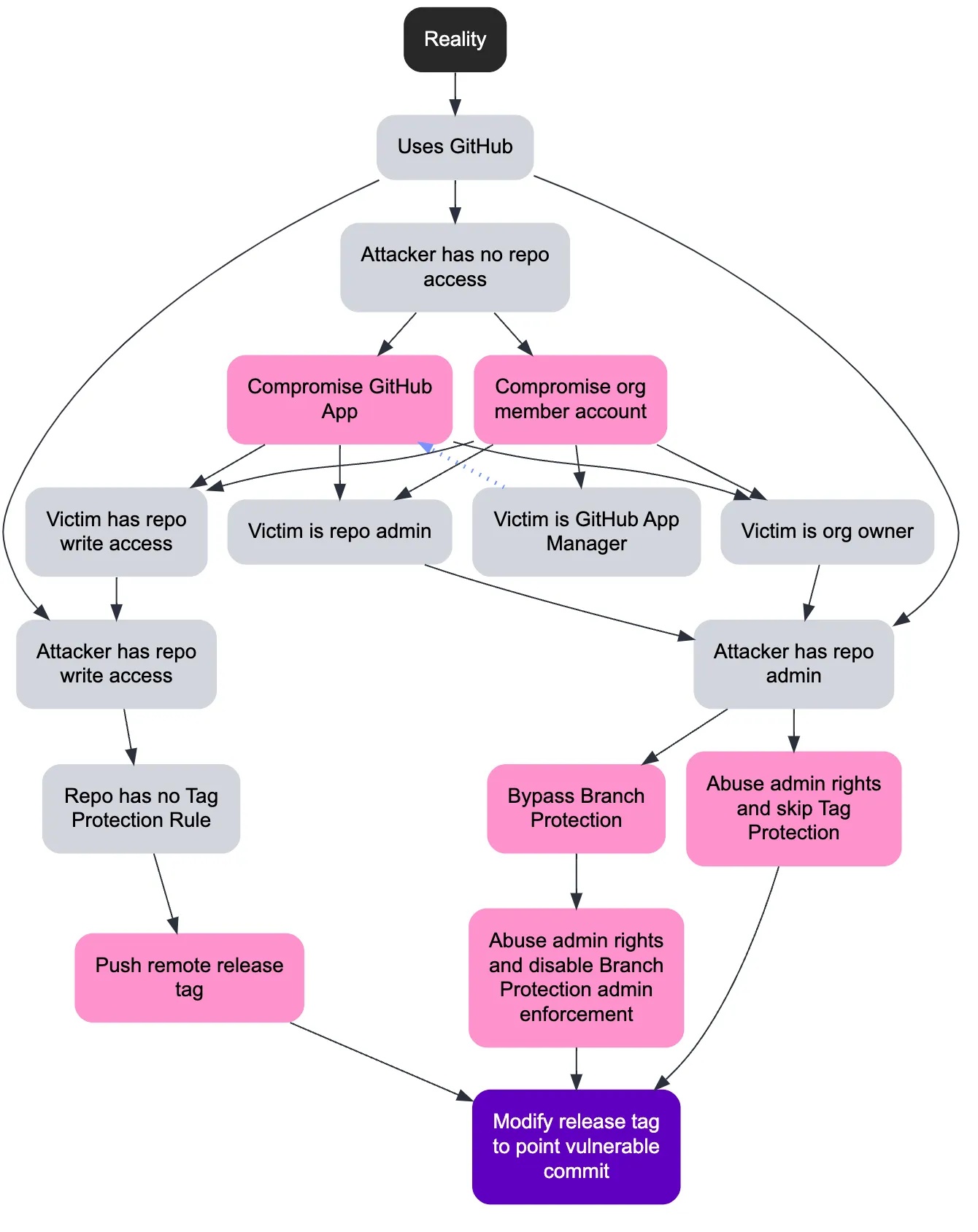
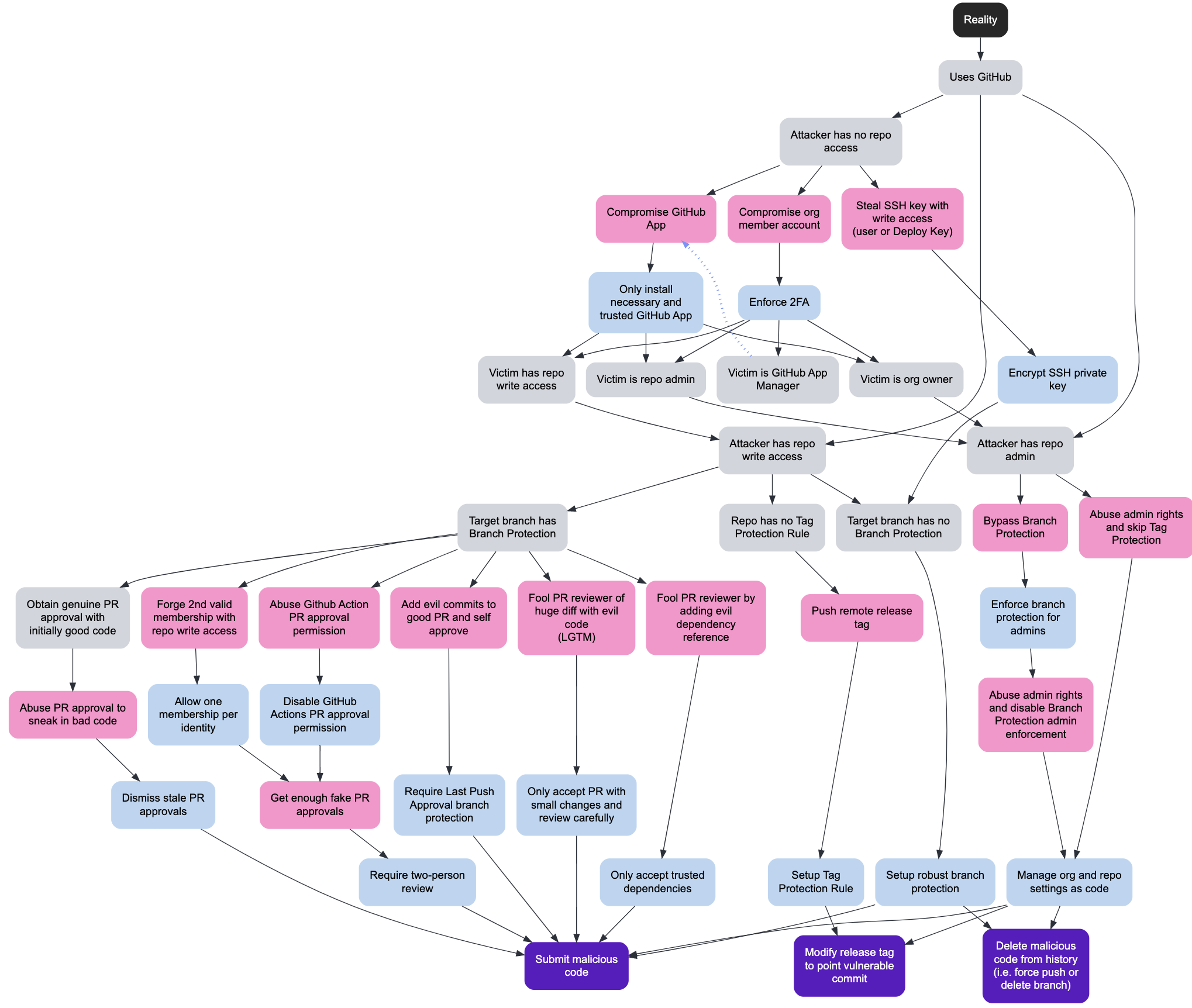
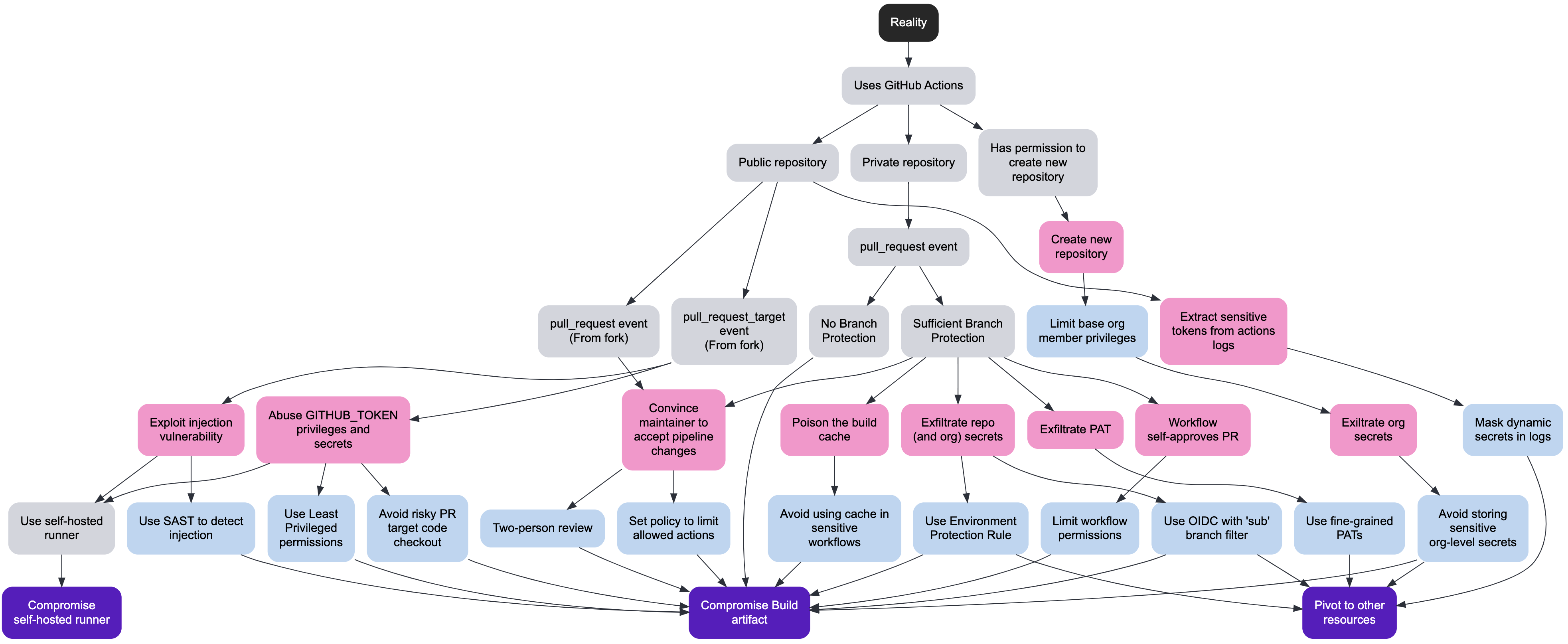
2025 didn't give us a new, magical Supply Chain vuln class; instead it gave us attackers who finally started reading our manuals. From Ultralytics' pull_request_target 0-day through Kong, tj-actions, GhostAction, Nx, GlassWorm and both Shai-Hulud waves, the common pattern wasn't typosquats but Pipeline Parasitism: living off CI/CD, maintainer accounts and developer endpoints using the same tools and patterns we published to defend them. The vuln mechanics stayed boring: shell injections and over-privileged tokens. But they were operationalized with worms, invisible Unicode payloads, blockchain C2, and even wiper failsafes. Thankfully, platforms are finally improving, yet "pwn request" is here to stay; the only sustainable answer is to treat pipelines as production systems and publish future research assuming adversaries are our most diligent readers!